:: source http://news.discovery.com/tech/my-favorite-hackers.html
Thu Dec 3, 2009 05:30 AM ET | content provided by Ryan Draga
as a self-proclaimed hacker, who means you no harm, I stand on the shoulders of giants. The following people have set the standard for hacking and have given all of us newbies something to the strive for. These are some of the Great Ones, the ones we admire, emulate. These are my favs.
1. Kevin Mitnick
The Man. The Myth. The Legend. This guy was the top hacker in the world for a good part of the late 70s and early 80s. He was one of the first, and in his time, gave the pre-silicon valley tech bigwigs a good shakedown. He broke into systems owned by Sun Microsystems, IBM, DEC, Motorola, and even managed (allegedly) to wiretap FBI conversations. He did time for it, but now works as a security consultant. Though most hackers today consider his technical knowledge to be archaic, he has one of the sharpest minds in social engineering even today.
WATCH VIDEO: Darren Kitchen, hacker and host of tech show Hak5, says why hacking isn't the same thing as cyber crime.
2. Fyodor
Fyodor, aka Gordon Lyon, gave us hackers one of our greatest tools. NMAP. NMAP is a powerful piece of software that lets us analyze the topography of any given network. With a quick nmap session, we can tell what Operating System is running on a given machine or set of machines, we can tell what services are running on the network, and we can tell what IP Addresses are active or inactive within any given network, among an infinite number of other functions. NMAP is indispensible and hackers would be virtually shooting in the dark without it. Today, Fyodor is responsible for overseeing the Honeynet Project, a distributed computing project that uses false open access points in a network (honeypots), to gather data regarding intrusion attempts on networks all over the world.
3. Michal Zalewski
Michal is currently in the employ of Google as a security researcher, but has been active in the hacker community since the early 90s as someone known for finding vulnerabilities where no one else could. His knowledge of web browser security is unparalleled.
4. Eric Corley
Eric founded the H.O.P.E. hacker conference as well as 2600: The Hacker Quarterly, a quarterly magazine about hacker culture. He's been an active member in the community since the 80s.
5. Solar Designer
Solar, aka Alexander Peslyak, is a Russian hacker responsible for the Openwall GNU/Linux project. Openwall is a Security-hardened Linux distribution meant for servers. In addition to his responsibilities with Openwall, he has been responsible for some of the most influential exploits within the Open Source community.
6. Robin Wood
Robin may be new to the scene, but he's definitely been talked about. You might remember me mentioning man-in-the-middle attacks and a piece of firmware called Jasager? Well, that's his baby. He wrote it and designed it. The man is a genius with anything wireless. Jasager's popularity though, is owed largely to the next name on the list.
7. Darren Kitchen
Darren is the host of Hak5, a web show dedicated to information security and generally making electronic devices do things they weren't intended to do. The show is hosted by Darren, Shannon Morse (aka Snubs) and Matt Lestock. Darren is to our community what Flava Flav was to Public Enemy, only, with more talent and without the myriad drug addictions. He always has his ear to the ground and always knows what's going on in the scene.
Ryan Draga lives in the suburbs of Toronto, Ontario, Canada and works as a system administrator for an insurance company, Kanetix, Ltd., and is also as a freelance IT/Information Security consultant under his own brand, Straylight Solutions. Visit his Web site, send a Twitter to @TuxOtaku or E-Mail at ryan.draga@tuxotaku.com.
Wednesday, March 17, 2010
Hackers for Hire
::source>>[http://liveshots.blogs.foxnews.com/2010/02/02/hackers-for-hire/?test=latestnews]
Hackers for Hire
February 2, 2010 - 1:59 PM | by: David Lee Miller
They go by names such as Piratecrackers, Yourhackers and Slickhackerz. Although illegal, a handful of internet services brazenly advertise that for a usual hundred dollar fee they can obtain almost any email password. One site boasts that it provides an ideal way to catch a cheating spouse or significant other.
George Washington University Law professor, Orrin Kerr who worked as a prosecutor specializing in computer crime said although these services are breaking the law, prosecuting them is “a low priority for law enforcement.” According to Kerr the crimes are hard to investigate because “not many victims know they have been victimized.”
Internet security consultant Kevin Mitnick, said these hackers for hire use “social engineering” rather than technology to hack into a victim’s email account. In other words they use elaborate trickery to fool people into revealing their passwords. Mitnick should know. He was once the FBI’s most wanted hacker. After serving five years in prison he turned his life around.
In order to expose how these hacker services work, Mitnick set up an email account for a fictitious girlfriend. He then asked the hackers to steal the password. Before the hackers could go to work they requested additional information. Mitnick received an email asking for the name of someone who was his girlfriend’s close friend.
According to Mitnick’s investigation, the hackers then send the intended target an electronic greeting card that appears to come from someone they know. By clicking on the link to view the e-greeting the victim is redirected to what looks like the sign on page for Google, AOL or whatever service the victim uses for email.
The site is a phony created by the hackers. Since the target is already signed into an email account re-entering a password should not be required. According to Mitnick, most people don’t hesitate to sign on again and re-enter their password. What they are really doing is sending it to the hackers.
The deception is called phishing. In order not to arouse any suspicion, the fake web site even produces the promised e-greeting, complete with music and animation.
Recognizing that potential customers might be understandably reluctant to pay prior to getting the hacked password, all of the hacking services ask for payment only after they provide proof of their success. Such proof can be a screen snap shot revealing the contents of the hacked account.
While law professor Kerrr said the hackers and the people who hire them are breaking the law, there is another reason not to employ hacking services. In some instances, Mitnick said the hackers threaten to contact the person hacked and to expose whoever hired them unless paid an additional fee. He says what began as email theft elevates to “cyber-extortion.”
In order to prevent falling victim to this or a similar scam Mitnick advises checking the browser address bar to confirm you are on the correct web page and not a lookalike. He also warns that if you have been re-directed from one site to another never enter a password or personal information.
Hackers for Hire
February 2, 2010 - 1:59 PM | by: David Lee Miller
They go by names such as Piratecrackers, Yourhackers and Slickhackerz. Although illegal, a handful of internet services brazenly advertise that for a usual hundred dollar fee they can obtain almost any email password. One site boasts that it provides an ideal way to catch a cheating spouse or significant other.
George Washington University Law professor, Orrin Kerr who worked as a prosecutor specializing in computer crime said although these services are breaking the law, prosecuting them is “a low priority for law enforcement.” According to Kerr the crimes are hard to investigate because “not many victims know they have been victimized.”
Internet security consultant Kevin Mitnick, said these hackers for hire use “social engineering” rather than technology to hack into a victim’s email account. In other words they use elaborate trickery to fool people into revealing their passwords. Mitnick should know. He was once the FBI’s most wanted hacker. After serving five years in prison he turned his life around.
In order to expose how these hacker services work, Mitnick set up an email account for a fictitious girlfriend. He then asked the hackers to steal the password. Before the hackers could go to work they requested additional information. Mitnick received an email asking for the name of someone who was his girlfriend’s close friend.
According to Mitnick’s investigation, the hackers then send the intended target an electronic greeting card that appears to come from someone they know. By clicking on the link to view the e-greeting the victim is redirected to what looks like the sign on page for Google, AOL or whatever service the victim uses for email.
The site is a phony created by the hackers. Since the target is already signed into an email account re-entering a password should not be required. According to Mitnick, most people don’t hesitate to sign on again and re-enter their password. What they are really doing is sending it to the hackers.
The deception is called phishing. In order not to arouse any suspicion, the fake web site even produces the promised e-greeting, complete with music and animation.
Recognizing that potential customers might be understandably reluctant to pay prior to getting the hacked password, all of the hacking services ask for payment only after they provide proof of their success. Such proof can be a screen snap shot revealing the contents of the hacked account.
While law professor Kerrr said the hackers and the people who hire them are breaking the law, there is another reason not to employ hacking services. In some instances, Mitnick said the hackers threaten to contact the person hacked and to expose whoever hired them unless paid an additional fee. He says what began as email theft elevates to “cyber-extortion.”
In order to prevent falling victim to this or a similar scam Mitnick advises checking the browser address bar to confirm you are on the correct web page and not a lookalike. He also warns that if you have been re-directed from one site to another never enter a password or personal information.
Wednesday, March 10, 2010
Malware Treats
Malware treats
Introduction
What is malware ? . malware is kind of software that be use for destroy, disturb ,or take in something that call as Malicious sofware to run in computer. malware treat can happen without owner of computer no it , can happen when user install anything software or application from internet for example when you downloading Java applet from web site while user viewing the websites million bytes of the data that you transfer maybe had been modification to you exciting file all happen without you occurring(p.pfleeeger2003,110) .Another thing that malicious can do is writing a massage on computer screen ,stopping and running the program ,generic a sound ,or erasing a stored file .The thing that I though great malicious do is take user authority for example malicious can touch same ways as user touch, and something use have might be out of control of dear safety because malicious can deleted , read, write ,the data without user permission . Actually malware not always dangerous but it just intrusive and irritate your computer
Virus evolution
Over 20 years only computer viruses evolve from urban legend into a real digital disease. Early virus started to invade computer when they were distributed in floppy disk which they reside in boot sector. The boot sector is load when computer are started thus ensuring the virus to be executed.
Later when the hardware evolve, and floppy disk are replaced by compact disk, which cannot be modified. The operating system are becoming more secure on boot sector, thus makes the virus dwindling.
The virus then advance into using e-mail to spread as year 1999 virus named Melissa and iloveyou virus in 2000 were develop using visual basic and pinned as attachment.(howstuffworks.com)
Early anti-virus was created to combat this syndrome by extracting the virus signature to detect the virus copies. Then the virus author encrypted them to hide the virus from the anti-virus.
Anti virus researcher then detect the decryption routine logic of the virus to identify them, until the coming of polymorphic virus, the anti-virus is no longer can use the finger print detection.
The anti-virus has to survive so they come out with emulator to make the virus reveal themselves.
Then virus increase the range by installed themselves in memory so they become stealth.
Anti virus today has developed to scan the memory, network packet and files.( csrc.nist.gov)
Table 1: Characteristics of Malware (source: P. Pfleeger, 2003)
Type Characteristics
virus - Attaches itself to program and copy itself to other program
Trojan horse - Contains unexpected ,additional functionality
Trapdoor - Allows unauthorized ,addition functionality
Backdoor - Allows unauthorized, converted channel
Adware /
spyware - Always Sit in free software
Buffer overflow - Insert malicious data value/instruction code
worm - Propagates copies itself thought network
· virus.
Long name for virus is Vital Information Resources Under Siege (). It call virus because it affect program acting like a biological virus that attack human body. Virus work by infection to the file that running the same time virus in memory ,when the file is infection ,it can spread infection to other files whenever it running. In long time ago virus spread by people using diskettes. but today it spread by CD, and downloading to transfer its self to another computer and automatically run by human .Virus actually
hard to detect, not easy destroy or deactivated ,it can spread infection widely, reinsert program, easily to create and machine and OS independent.
HOW VIRUS WORK
Virus work by tree ways
1) via attach
· 1.1Append to program e-mail
· 1.2 Viruses that surround a program
· 1.3 Integrated viruses and replacements program code
2)Gain control
· Virus replaces target
2) Reside
· In boot sector
· Memory
· Application program
· Libraries
Types of virus
· Boot virus
Boot sector viruses is exist in specific area in PC hard disk, that read and executed
by computer in boot time, actually boot virus infect DOS boot sector only at the same time as a subtype called the MBR virus infects the master boot record .virus is loaded into memory when both of these area of the hard disk are read during, boot process(kb.iu.edu.)
Impaction
A boot sector virus can cause a lot problem to the data for example data can disappear from their entire part, it also can make computer in unstable such as computer might be fails to start up or find the hard drive ,it can cause an error messages such as “ Invalid system disk” could turn into rife, and it also is hard to remove .( kb.iu.edMemory
· Resident virus
Memory resident virus spread is infect the volatile space of Ram,it run automatically when program run. they no memory resident viruses do not infect computer memory being active during finite period.( p.pfleeeger2003)
· Marco viruses
Marco virus are virus that in “document” –file created in different application that do not include only data but also macro. It can spread from one document or computer to another.
Most macro viruses are written to work in Microsoft application such as word or excel or PowerPoint.( avast)
· Polymorphic Virus
Plymorphic computer virus is the complex and difficult to detect, by scanning because each copy of the virus looks different than the othVirus Signatures
-Virus signatures is characteristic or identity for virus ,
-it is important to for creating a program ,called virus scanner that can automatically detect and ,and remove viruses .
for example a scanner look for sign of the code red worm can look for a
paten containing the following characters:
-When scanner recognize a know virus pattern it can block virus ,inform the user to delete or remove the virus (p.pfleeeger2003)

· WORM
Worm is actually self – replicating virus that can spread from one computer to others without any help from human, it usually spread from e-mail attachment.
What will happen when you attach the e-mail that have worm virus: ()
For example the attachment is called Simpson Episodes. When Simpson Episodes executed,()
The worm will launch Internet Browser and open a fan site for tv show The Simpson.
A process attached to the mail will open Outlook Express and send mail to everyone in your address book. If you try to quit the Outlook Express, the worm will re launch it.
The worm will put a copy of itself in your Startup Items folder, so when you restart your computer, the worm automatically runs.

FIigure:1 Example of detected worm by an antivirus(source: komotv)

Figure:2Example command for worm
· ADWARE
Adware short name for ADvertisement SoftWARE it same as spyware it be installed to your computer to show the advisement by sending unwanted popping onto your computer screen
and it might be slow your computer internet connection ,
not all adware is bad ,because same adware that have install itself if your system give permission
· Difference between spyware and adware
spyware – collects personal information about you example keyloggers to take what were word,our numbers when you touch the keyboard
adware – put ads up on your screen such as free screen server

Figure 3 : advertisement pop up on your computer screen: Example of adware
HOW TO REMOWE SPYWARE
Usually use antispyware to remove spawaren for example by using spybot antispaware

· SALAMI ATTACK
Salami attack is a attack by number of dollar cent of money of banking system, like take a money small amount money from awful a lot of account in the banking system
The banking programmer can do salami attack by rounding some amount money example:
$10,000.054 to $10,000.04
Which is the banking programmer stealing $0.001 cents from rounding that number , this attack is very hard to detected .

· TROJAN
History of Trojan Horse
Trojan horse is attributed from Daniel Edward of NSA , take the name from the legend of TROJAN WAR history , in the war Geek build the very big wooden horse as strategic to win the war , the wooden horse is give to the Greek enemy as the present for offering a peace but inside the wooden horse have a lot of Greek soldier ,so went the wooden horse enter the TROY CITY , in night Greek soldier come out from the wooden horse and the war begin .
It like look good at outside but have bad inside
How Trojan infected
Example of Trojan attack is by sending greeting card ,went victim attach it ,Trojan start executables or copied to victim computer
In window you can see executable program have file extension like
exe, vbs, com, bat,ect an some of this file extension might be Trojan . such as Svchost32.exe,back.exe

Figure:4:exe.file as Trojan
Trojan can spread it self to guise of literally, such as free game, movie or song. It actually that vitim download it from www,or FTP, which is famous platform for trojan to find victim .
It also can act like a important massages that have trojan one of it treat in this era .
Types of Trojan horse payload
· Remote Access
· Email Sending
· Data Destructive
· Downloader
· Proxy Trojan (disguising others as the infected computer)
· denial-of-service attack (DoS
FTP Trojan (adding or copying data from the infected computer
· security software disabler
· URL trojan (directing the infected computer to only connect to the internet via an expensive dial-up connection).
· EXAMPLE OF TROJAN FAMOUS TROJAN
§ Subseven Trojan Server & Client
§ Downloader-ev
§ Pest trap
§ NetBus
§ Flooder
§ Tagasaurus

Subseven Trojan usually use by hacking to attack the computer vitim ,by enter the backdoor port ,27374 .
· HOW TO A VOID FROM GATTING INFECTED FROM FUTURE
· FIRST make check while download something from people ,our web site
· Make sure what the file is before open it, even it came from your friend, because Trojan usually spread to friend account e-mail, scan it with anti virus .
· Beware of hidden file exertion ,because Trojan may executed their self
· Never type command that other ask to type it, or go to stranger web
Introduction
What is malware ? . malware is kind of software that be use for destroy, disturb ,or take in something that call as Malicious sofware to run in computer. malware treat can happen without owner of computer no it , can happen when user install anything software or application from internet for example when you downloading Java applet from web site while user viewing the websites million bytes of the data that you transfer maybe had been modification to you exciting file all happen without you occurring(p.pfleeeger2003,110) .Another thing that malicious can do is writing a massage on computer screen ,stopping and running the program ,generic a sound ,or erasing a stored file .The thing that I though great malicious do is take user authority for example malicious can touch same ways as user touch, and something use have might be out of control of dear safety because malicious can deleted , read, write ,the data without user permission . Actually malware not always dangerous but it just intrusive and irritate your computer
Virus evolution
Over 20 years only computer viruses evolve from urban legend into a real digital disease. Early virus started to invade computer when they were distributed in floppy disk which they reside in boot sector. The boot sector is load when computer are started thus ensuring the virus to be executed.
Later when the hardware evolve, and floppy disk are replaced by compact disk, which cannot be modified. The operating system are becoming more secure on boot sector, thus makes the virus dwindling.
The virus then advance into using e-mail to spread as year 1999 virus named Melissa and iloveyou virus in 2000 were develop using visual basic and pinned as attachment.(howstuffworks.com)
Early anti-virus was created to combat this syndrome by extracting the virus signature to detect the virus copies. Then the virus author encrypted them to hide the virus from the anti-virus.
Anti virus researcher then detect the decryption routine logic of the virus to identify them, until the coming of polymorphic virus, the anti-virus is no longer can use the finger print detection.
The anti-virus has to survive so they come out with emulator to make the virus reveal themselves.
Then virus increase the range by installed themselves in memory so they become stealth.
Anti virus today has developed to scan the memory, network packet and files.( csrc.nist.gov)
Table 1: Characteristics of Malware (source: P. Pfleeger, 2003)
Type Characteristics
virus - Attaches itself to program and copy itself to other program
Trojan horse - Contains unexpected ,additional functionality
Trapdoor - Allows unauthorized ,addition functionality
Backdoor - Allows unauthorized, converted channel
Adware /
spyware - Always Sit in free software
Buffer overflow - Insert malicious data value/instruction code
worm - Propagates copies itself thought network
· virus.
Long name for virus is Vital Information Resources Under Siege (). It call virus because it affect program acting like a biological virus that attack human body. Virus work by infection to the file that running the same time virus in memory ,when the file is infection ,it can spread infection to other files whenever it running. In long time ago virus spread by people using diskettes. but today it spread by CD, and downloading to transfer its self to another computer and automatically run by human .Virus actually
hard to detect, not easy destroy or deactivated ,it can spread infection widely, reinsert program, easily to create and machine and OS independent.
HOW VIRUS WORK
Virus work by tree ways
1) via attach
· 1.1Append to program e-mail
· 1.2 Viruses that surround a program
· 1.3 Integrated viruses and replacements program code
2)Gain control
· Virus replaces target
2) Reside
· In boot sector
· Memory
· Application program
· Libraries
Types of virus
· Boot virus
Boot sector viruses is exist in specific area in PC hard disk, that read and executed
by computer in boot time, actually boot virus infect DOS boot sector only at the same time as a subtype called the MBR virus infects the master boot record .virus is loaded into memory when both of these area of the hard disk are read during, boot process(kb.iu.edu.)
Impaction
A boot sector virus can cause a lot problem to the data for example data can disappear from their entire part, it also can make computer in unstable such as computer might be fails to start up or find the hard drive ,it can cause an error messages such as “ Invalid system disk” could turn into rife, and it also is hard to remove .( kb.iu.edMemory
· Resident virus
Memory resident virus spread is infect the volatile space of Ram,it run automatically when program run. they no memory resident viruses do not infect computer memory being active during finite period.( p.pfleeeger2003)
· Marco viruses
Marco virus are virus that in “document” –file created in different application that do not include only data but also macro. It can spread from one document or computer to another.
Most macro viruses are written to work in Microsoft application such as word or excel or PowerPoint.( avast)
· Polymorphic Virus
Plymorphic computer virus is the complex and difficult to detect, by scanning because each copy of the virus looks different than the othVirus Signatures
-Virus signatures is characteristic or identity for virus ,
-it is important to for creating a program ,called virus scanner that can automatically detect and ,and remove viruses .
for example a scanner look for sign of the code red worm can look for a
paten containing the following characters:
-When scanner recognize a know virus pattern it can block virus ,inform the user to delete or remove the virus (p.pfleeeger2003)

· WORM
Worm is actually self – replicating virus that can spread from one computer to others without any help from human, it usually spread from e-mail attachment.
What will happen when you attach the e-mail that have worm virus: ()
For example the attachment is called Simpson Episodes. When Simpson Episodes executed,()
The worm will launch Internet Browser and open a fan site for tv show The Simpson.
A process attached to the mail will open Outlook Express and send mail to everyone in your address book. If you try to quit the Outlook Express, the worm will re launch it.
The worm will put a copy of itself in your Startup Items folder, so when you restart your computer, the worm automatically runs.

FIigure:1 Example of detected worm by an antivirus(source: komotv)

Figure:2Example command for worm
· ADWARE
Adware short name for ADvertisement SoftWARE it same as spyware it be installed to your computer to show the advisement by sending unwanted popping onto your computer screen
and it might be slow your computer internet connection ,
not all adware is bad ,because same adware that have install itself if your system give permission
· Difference between spyware and adware
spyware – collects personal information about you example keyloggers to take what were word,our numbers when you touch the keyboard
adware – put ads up on your screen such as free screen server

Figure 3 : advertisement pop up on your computer screen: Example of adware
HOW TO REMOWE SPYWARE
Usually use antispyware to remove spawaren for example by using spybot antispaware

· SALAMI ATTACK
Salami attack is a attack by number of dollar cent of money of banking system, like take a money small amount money from awful a lot of account in the banking system
The banking programmer can do salami attack by rounding some amount money example:
$10,000.054 to $10,000.04
Which is the banking programmer stealing $0.001 cents from rounding that number , this attack is very hard to detected .

· TROJAN
History of Trojan Horse
Trojan horse is attributed from Daniel Edward of NSA , take the name from the legend of TROJAN WAR history , in the war Geek build the very big wooden horse as strategic to win the war , the wooden horse is give to the Greek enemy as the present for offering a peace but inside the wooden horse have a lot of Greek soldier ,so went the wooden horse enter the TROY CITY , in night Greek soldier come out from the wooden horse and the war begin .
It like look good at outside but have bad inside
How Trojan infected
Example of Trojan attack is by sending greeting card ,went victim attach it ,Trojan start executables or copied to victim computer
In window you can see executable program have file extension like
exe, vbs, com, bat,ect an some of this file extension might be Trojan . such as Svchost32.exe,back.exe

Figure:4:exe.file as Trojan
Trojan can spread it self to guise of literally, such as free game, movie or song. It actually that vitim download it from www,or FTP, which is famous platform for trojan to find victim .
It also can act like a important massages that have trojan one of it treat in this era .
Types of Trojan horse payload
· Remote Access
· Email Sending
· Data Destructive
· Downloader
· Proxy Trojan (disguising others as the infected computer)
· denial-of-service attack (DoS
FTP Trojan (adding or copying data from the infected computer
· security software disabler
· URL trojan (directing the infected computer to only connect to the internet via an expensive dial-up connection).
· EXAMPLE OF TROJAN FAMOUS TROJAN
§ Subseven Trojan Server & Client
§ Downloader-ev
§ Pest trap
§ NetBus
§ Flooder
§ Tagasaurus

Subseven Trojan usually use by hacking to attack the computer vitim ,by enter the backdoor port ,27374 .
· HOW TO A VOID FROM GATTING INFECTED FROM FUTURE
· FIRST make check while download something from people ,our web site
· Make sure what the file is before open it, even it came from your friend, because Trojan usually spread to friend account e-mail, scan it with anti virus .
· Beware of hidden file exertion ,because Trojan may executed their self
· Never type command that other ask to type it, or go to stranger web
Tuesday, March 9, 2010
Brutus
Brutus is an oline or remote password cracker
is actually recover valid access token[username and password]
it avaible for window
it curently release including this currently authentication type [HTTP,POP3,FTP,SMB,Telnet,NETbios]Is the kind of real outside attack
Brutus can be run in single user mode means that is trying to break into single account by tring different password combination or trying list of user/ password combination from a word file ,the application scans the host for know services and can be easily customizaed to break -in any others custom service requiring interactive logon of user name and password.
by means that brutus can do dictionary attack
You can get some good password list at= packetstormsecurity.org ,millw0rm website
Brutus also can do Brute force attack[it can crack any password by trying any possible combination of letter ,number,and special character until password is found and maybe take long time

Simple step using brutus
You can get Brutus at http://www.hobbie.net/brutus/
- make sure you disable your anti -virus program when you decide to download and explore brutus
- second choose a target [ depend on you as far as brutus concerned a target is remote system and remote user on a remode system ,there is more
- in this case i choose target is =person ip adress ,by taken from randomly using port scan[Advance Port Scanner.exe]

-then choose the pass mode word list and browse and select the file containing you word list ,get good password list at http://packetstormsecurity.org/Crackers/wordlists/
- then browse it whre you put your password list.txt and user file.txt
-once you hit start the program will attempt to connect to the server and begin to try all the possible combinations from you lists then get the result
Below show the step

Below show the result i get

- if you lucky you will get right the username and password
- finally use a proxy when using a program like this [ proxy is cloaks your ip address by sending your connection request through another computer before going to target]
is actually recover valid access token[username and password]
it avaible for window
it curently release including this currently authentication type [HTTP,POP3,FTP,SMB,Telnet,NETbios]Is the kind of real outside attack
Brutus can be run in single user mode means that is trying to break into single account by tring different password combination or trying list of user/ password combination from a word file ,the application scans the host for know services and can be easily customizaed to break -in any others custom service requiring interactive logon of user name and password.
by means that brutus can do dictionary attack
You can get some good password list at= packetstormsecurity.org ,millw0rm website
Brutus also can do Brute force attack[it can crack any password by trying any possible combination of letter ,number,and special character until password is found and maybe take long time

Simple step using brutus
You can get Brutus at http://www.hobbie.net/brutus/
- make sure you disable your anti -virus program when you decide to download and explore brutus
- second choose a target [ depend on you as far as brutus concerned a target is remote system and remote user on a remode system ,there is more
- in this case i choose target is =person ip adress ,by taken from randomly using port scan[Advance Port Scanner.exe]

-then choose the pass mode word list and browse and select the file containing you word list ,get good password list at http://packetstormsecurity.org/Crackers/wordlists/
- then browse it whre you put your password list.txt and user file.txt
-once you hit start the program will attempt to connect to the server and begin to try all the possible combinations from you lists then get the result
Below show the step

Below show the result i get

- if you lucky you will get right the username and password
- finally use a proxy when using a program like this [ proxy is cloaks your ip address by sending your connection request through another computer before going to target]
Yahoo Booter
Example yahoo booters

Yahoo booter is a software program used by maniacs around the world to'boot'(kick) others users out of the yahoo messenger program
it actually programmed in vb.net because GUi features available and vb tunneling abilities
there are different type of yahoo booters.
ping
multibot
singlebot
Ymlite
Tunnel
Audible
Im booters
The main essential thing for booters that you as a user will need is "bots" which is yahoo id's
To protect from yahoo booters
Yahoo Messenger>> Massenger>>Preferences>>Ignore List>>Ignore anyone who is not on my Messenger List

Yahoo booter is a software program used by maniacs around the world to'boot'(kick) others users out of the yahoo messenger program
it actually programmed in vb.net because GUi features available and vb tunneling abilities
there are different type of yahoo booters.
ping
multibot
singlebot
Ymlite
Tunnel
Audible
Im booters
The main essential thing for booters that you as a user will need is "bots" which is yahoo id's
To protect from yahoo booters
Yahoo Messenger>> Massenger>>Preferences>>Ignore List>>Ignore anyone who is not on my Messenger List
Sunday, March 7, 2010
computer remote - Team Viewer
Intro
first of all ,it actually another software that i have learn from my friend ,hehhehe
let start .....
About Team Viewer
Team viewer is software that view you computer desktop in the network ,meaning that you can sharing full akses of your computer with you friend .
team view may help you to solve problems that require access Dekstop in full on a computer with a different network.
Team view is divide into two which is host and client.
Host is play as server or monitor in you computer
client is as computer that want to be remote , it be install to that computer
How to use it
go to this web :http://www.teamviewer.com/download/index.aspx
download the Team view host and install it in your computer/ or computer that play as server or monitor

then install the client to the computer that want be remote
the you will the ID and password that will as transaction between server and client

In the computer server that install host , enter the client ID and click the connect to partner

then a few second it will appear window team view authentication that force to enter the password from client computer
and finis , you can start remote you friend computer :)
first of all ,it actually another software that i have learn from my friend ,hehhehe
let start .....
About Team Viewer
Team viewer is software that view you computer desktop in the network ,meaning that you can sharing full akses of your computer with you friend .
team view may help you to solve problems that require access Dekstop in full on a computer with a different network.
Team view is divide into two which is host and client.
Host is play as server or monitor in you computer
client is as computer that want to be remote , it be install to that computer
How to use it
go to this web :http://www.teamviewer.com/download/index.aspx
download the Team view host and install it in your computer/ or computer that play as server or monitor

then install the client to the computer that want be remote
the you will the ID and password that will as transaction between server and client

In the computer server that install host , enter the client ID and click the connect to partner

then a few second it will appear window team view authentication that force to enter the password from client computer
and finis , you can start remote you friend computer :)
Thursday, March 4, 2010
Md5 Online crack
Router Configuration
1. Enter global configuration mode.
router> enable
router# config t
2. Configure hostname and passwords.
router(config)#hostname Lab-B
Lab-B(config)#enable secret class
Lab-B(config)#enable password cisco
3. Configure the interfaces.
Lab-B(config)#int fastethernet0/0
Lab-B(config-if)#ip address 219.17.100.1 255.255.255.0
Lab-B(config-if)#no shutdownLab-B(config)#int s0/0
Lab-B(config-if)#ip address 199.6.13.1 255.255.255.0
Lab-B(config-if)#clock rate 56000Lab-B(config-if)#bandwidth 56
Lab-B(config-if)#no shutdownLab-B(config)#int s1
Lab-B(config-if)#ip address 201.100.11.2 255.255.255.0
Lab-B(config-if)#no shutdownLab-B(config-if)#exit
4. Configure the routing protocol and table.
Lab-B(config)#ip host Lab-A 192.5.5.1 205.7.5.1 201.100.11.1
Lab-B(config)#ip host Lab-B 219.17.100.1 199.6.13.1 201.100.11.2
Lab-B(config)#ip host Lab-C 223.8.151.1 204.204.7.1 199.6.13.2
Lab-B(config)#ip host Lab-D 210.93.105.1 204.204.7.2
Lab-B(config)#ip host Lab-E 210.93.105.2
6. Configure the line con 0 and line vty 0 4 (the telnet login).
Lab-B(config)#line con 0
Lab-B(config-line)#login
Lab-B(config-line)#password cisco
Lab-B(config-line)#line vty 0 4
Lab-B(config-line)#login
Lab-B(config-line)#password cisco
Lab-B(config-line)#exit
Lab-B(config)#exit
Lab-B#
7. Save the running configuration to NVRAM
Lab-B#copy run start
router> enable
router# config t
2. Configure hostname and passwords.
router(config)#hostname Lab-B
Lab-B(config)#enable secret class
Lab-B(config)#enable password cisco
3. Configure the interfaces.
Lab-B(config)#int fastethernet0/0
Lab-B(config-if)#ip address 219.17.100.1 255.255.255.0
Lab-B(config-if)#no shutdownLab-B(config)#int s0/0
Lab-B(config-if)#ip address 199.6.13.1 255.255.255.0
Lab-B(config-if)#clock rate 56000Lab-B(config-if)#bandwidth 56
Lab-B(config-if)#no shutdownLab-B(config)#int s1
Lab-B(config-if)#ip address 201.100.11.2 255.255.255.0
Lab-B(config-if)#no shutdownLab-B(config-if)#exit
4. Configure the routing protocol and table.
Lab-B(config)#ip host Lab-A 192.5.5.1 205.7.5.1 201.100.11.1
Lab-B(config)#ip host Lab-B 219.17.100.1 199.6.13.1 201.100.11.2
Lab-B(config)#ip host Lab-C 223.8.151.1 204.204.7.1 199.6.13.2
Lab-B(config)#ip host Lab-D 210.93.105.1 204.204.7.2
Lab-B(config)#ip host Lab-E 210.93.105.2
6. Configure the line con 0 and line vty 0 4 (the telnet login).
Lab-B(config)#line con 0
Lab-B(config-line)#login
Lab-B(config-line)#password cisco
Lab-B(config-line)#line vty 0 4
Lab-B(config-line)#login
Lab-B(config-line)#password cisco
Lab-B(config-line)#exit
Lab-B(config)#exit
Lab-B#
7. Save the running configuration to NVRAM
Lab-B#copy run start
Palindrome
import java.util.*;
public class Palindrome
{
public static void main(String[] args)
{
String deLimiters = ";:'<>,./?-+!@#$%^&*() ";
Stack stack = new Stack();
Scanner reader = new Scanner(System.in);
while(true)
{
String palindrome = "";
String backwards = "";
System.out.println("Please enter a palindrome (Type n to quit): ");
String str = reader.nextLine();
if(str.equalsIgnoreCase("n"))
{
System.exit(0);
}
StringTokenizer tokens = new StringTokenizer(str, deLimiters);
StringTokenizer tokens2 = new StringTokenizer(palindrome, deLimiters);
while(tokens.hasMoreTokens())
{
palindrome += tokens.nextToken();
}
for(int i = 0; i < palindrome.length(); i++)
{
stack.add(palindrome.substring(i, i +1));
}
while(! stack.empty())
{
backwards += stack.pop();
}
if(palindrome.equalsIgnoreCase(backwards))
{
System.out.println("Your phrase: " + palindrome + " is a Palindrome");
}
else
{
System.out.println("Your phrase: " + palindrome + " is not a Palindrome");
}
}
}
}
OUTPUT
--------------------Configuration:--------------------
Please enter a palindrome (Type n to quit):
SAYA
Your phrase: SAYA is not a Palindrome
Please enter a palindrome (Type n to quit):
KAKAK
Your phrase: KAKAK is a Palindrome
Please enter a palindrome (Type n to quit):
N
Process completed.
public class Palindrome
{
public static void main(String[] args)
{
String deLimiters = ";:'<>,./?-+!@#$%^&*() ";
Stack
Scanner reader = new Scanner(System.in);
while(true)
{
String palindrome = "";
String backwards = "";
System.out.println("Please enter a palindrome (Type n to quit): ");
String str = reader.nextLine();
if(str.equalsIgnoreCase("n"))
{
System.exit(0);
}
StringTokenizer tokens = new StringTokenizer(str, deLimiters);
StringTokenizer tokens2 = new StringTokenizer(palindrome, deLimiters);
while(tokens.hasMoreTokens())
{
palindrome += tokens.nextToken();
}
for(int i = 0; i < palindrome.length(); i++)
{
stack.add(palindrome.substring(i, i +1));
}
while(! stack.empty())
{
backwards += stack.pop();
}
if(palindrome.equalsIgnoreCase(backwards))
{
System.out.println("Your phrase: " + palindrome + " is a Palindrome");
}
else
{
System.out.println("Your phrase: " + palindrome + " is not a Palindrome");
}
}
}
}
OUTPUT
--------------------Configuration:
Please enter a palindrome (Type n to quit):
SAYA
Your phrase: SAYA is not a Palindrome
Please enter a palindrome (Type n to quit):
KAKAK
Your phrase: KAKAK is a Palindrome
Please enter a palindrome (Type n to quit):
N
Process completed.
Gcd_Algorithm
public class Gcd_Algorithm
{
//Method Iterator for Great Common Divisor
public static long iteration (long a, long b)
{
int gcd = 1;
int k = 1;
while (k <= a && k <= b)
{
if (a % k == 0 && b % k == 0)
gcd = k;
k++;
}
System.out.print("\nGreat Common Divisor in iteration method : " + gcd);
return gcd;
}
//Method Recursive
public static long recursion (long a, long b)
{
long gcd = 0;
long r = 0;
a = Math.abs (a);
b = Math.abs (b);
if (b == 0)
{
gcd = a; //if n == 0, then m = gcd
System.out.println ("\nGreat Common Divisor in recursive method : " + gcd);
}
else
{
gcd = recursion(b, a % b); //invoke recursive method, and return value n
}
return gcd;
}
}
import java.util.*;
public class Main
{
public static void main (String [] args)
{
Gcd_Algorithm gcd = new Gcd_Algorithm();
Scanner myscanner = new Scanner (System.in);
System.out.print ("Please enter value of a:");
long a = myscanner.nextInt(); //input m value
System.out.print ("Please enter value of b:");
long b = myscanner.nextInt(); //input n value
gcd.iteration(a, b); //invoke to iteration method
gcd.recursion(a, b); //invoke to recursion method
}
}
OUTPUT
--------------------Configuration:--------------------
Please enter value of a:3
Please enter value of b:5
Great Common Divisor in iteration method : 1
Great Common Divisor in recursive method : 1
Process completed.
{
//Method Iterator for Great Common Divisor
public static long iteration (long a, long b)
{
int gcd = 1;
int k = 1;
while (k <= a && k <= b)
{
if (a % k == 0 && b % k == 0)
gcd = k;
k++;
}
System.out.print("\nGreat Common Divisor in iteration method : " + gcd);
return gcd;
}
//Method Recursive
public static long recursion (long a, long b)
{
long gcd = 0;
long r = 0;
a = Math.abs (a);
b = Math.abs (b);
if (b == 0)
{
gcd = a; //if n == 0, then m = gcd
System.out.println ("\nGreat Common Divisor in recursive method : " + gcd);
}
else
{
gcd = recursion(b, a % b); //invoke recursive method, and return value n
}
return gcd;
}
}
import java.util.*;
public class Main
{
public static void main (String [] args)
{
Gcd_Algorithm gcd = new Gcd_Algorithm();
Scanner myscanner = new Scanner (System.in);
System.out.print ("Please enter value of a:");
long a = myscanner.nextInt(); //input m value
System.out.print ("Please enter value of b:");
long b = myscanner.nextInt(); //input n value
gcd.iteration(a, b); //invoke to iteration method
gcd.recursion(a, b); //invoke to recursion method
}
}
OUTPUT
--------------------Configuration:
Please enter value of a:3
Please enter value of b:5
Great Common Divisor in iteration method : 1
Great Common Divisor in recursive method : 1
Process completed.
Tuesday, March 2, 2010
Prc View

Intro
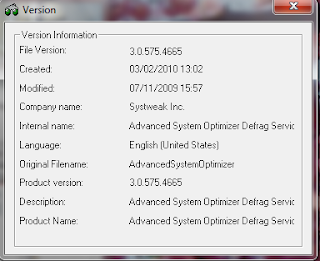
Prc View is a process viewer utility that displays detailed information about processes running under Windows.
screen shot
it portable ,just run it click the setup then you can kill the process that you want
you also can know detail of version info of process that you select ,by click on it for example
from that you can trace whether process that run is malware or not .......................... beside do kill the process Prc View can be malware countermeasures.
captive portal
Intro
again ,been blur , di pendek kan cerite , hahaha aku blur ape tu captive portal ,so my friend again teach me ,[ although is small info ,for me is big]
so google it oooooo now i understand
actualy captive portal is actualy like web page that you have to log in before using internet normally emm for more explain go to http://dev.wifidog.org/
as example

again ,been blur , di pendek kan cerite , hahaha aku blur ape tu captive portal ,so my friend again teach me ,[ although is small info ,for me is big]
so google it oooooo now i understand
actualy captive portal is actualy like web page that you have to log in before using internet normally emm for more explain go to http://dev.wifidog.org/
as example

Bandwidth speed Test
Intro
Bandwidth = a rate of data transfer, throughput or bit rate,
test your bandwidth speed [emmm today i want to share where you can test your bandwidth speed that i have learn from my friend , as usual i always blur 2 :) it happen when my friend ask me how your download speed and upload speed ??? so my friend explain to me ,aaah hahhaa ,now i know ]
for me just google hehee eg web:
http://www.speedtest.net/
http://speedtest.izzi.com.my/
http://www.bandwidthplace.com/
and other >>>>>>
example speed test webside
 or download bandwidth monitor at:-
or download bandwidth monitor at:-
http://www.bwmonitor.com/ }
http://www.brothersoft.com/downloads/bandwidth-monitor.html } Just for example
Bandwidth = a rate of data transfer, throughput or bit rate,
test your bandwidth speed [emmm today i want to share where you can test your bandwidth speed that i have learn from my friend , as usual i always blur 2 :) it happen when my friend ask me how your download speed and upload speed ??? so my friend explain to me ,aaah hahhaa ,now i know ]
for me just google hehee eg web:
http://www.speedtest.net/
http://speedtest.izzi.com.my/
http://www.bandwidthplace.com/
and other >>>>>>
example speed test webside
 or download bandwidth monitor at:-
or download bandwidth monitor at:-http://www.bwmonitor.com/ }
http://www.brothersoft.com/downloads/bandwidth-monitor.html } Just for example
Subscribe to:
Posts (Atom)